Mastering email security: Essential DNS records for email protection
Since email has been a vital means of communication for individuals and businesses, it is undoubtedly important to secure email communications to avoid malicious activities like phishing. One of the most effective methods to do so is the configuration of the right DNS records (SPF, DKIM, and DMARC). In this article, the details about email DNS records and how to implement them for a safe email will be explained.
In this article, you will read about:
The importance of email security
Email is one of the safest ways of communication, and tones of information are sent and received daily. Hence, it is a high priority to keep it safe to avoid any risk that may happen due to insecure emails. Another reason, which highlights the importance of email security, is the higher chance of reaching emails in “Inbox”, not in spam boxes. This also reduces the probability of getting blocked or filtered. In addition, with secured emails, the risk of unauthorized use of a domain for sending emails will be reduced which can help a domain or an IP address not lose credit. Moreover, email authentication can impact the level of trust and reliability in customers (email receivers) to open and read the email content instead of deleting or blocking that email.
There are also third-party email blacklist services like Spamcop, Senderbase, and Composite Blocking List (CBL) that have a large database of suspicious or spam IPs and domains and provide services to the email service providers such as Gmail and Yahoo. To avoid not being in these email blacklists, it is necessary to follow the email security instructions.
Essential DNS records for email protection
There are three essential DNS records to authenticate email senders and reduce threats:
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM)
- Domain-based Message Authentication, Reporting, & Conformance (DMARC)
1. SPF record
SPF is a TXT that contains a list of IP addresses (domains and mail servers) that are allowed to send emails on behalf of a domain. The email receiver server after receiving checks if the sender IP is in the SPF list or not.
How to set up an SPF record for your domain?
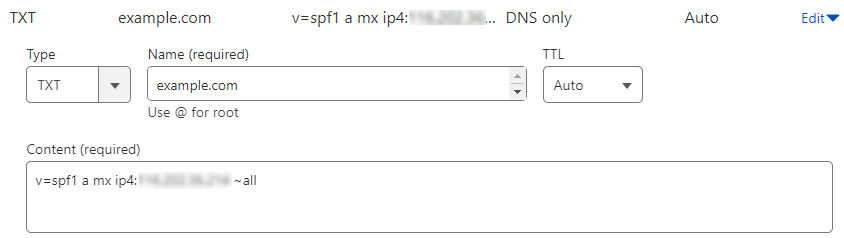
To set up an SPF record for your domain, first, you need to define a DNS TXT record and add a value like the example below:
v=spf1 a mx ip4:51.79.69.59 ~all
v=spf1 ip4:192.168.0.0/16 include:_spf.google.com ~allSPF tags details:
SPF version: The v=spf1 is the version of the SPF.
a: The a allows all the servers that are defined in an A record of a domain to send emails to that server.
mx: The mx helps the email receiver server to authorize the sender’s address using MX records (it contains the mail server’s DNS information).
ip4 or ip6: This is the email sender’s server IP address that can be ipv4 or ipv6.
include: If you send emails from other servers and third parties, you can use include to add them.
(-): By using (-) in the SPF records, all the emails that come from another address, which are not listed in the SPF record IP list, will be rejected by the email receiver (Higher safety).
v=spf1 a mx ip4:51.79.69.59 -all(~): By using (~) in the SPF record, the messages that do not come from the addresses listed in the record will be received but they will get flagged as a suspicious source (lower safety).
v=spf1 a mx ip4:51.79.69.59 ~allall: It comes at the end of the SPF and can have different effects based on the mechanisms (-) or (~) used before it. The -all or ~all specifies how the receiver server should behave against unauthorized emails.
2. DKIM record
DKIM is another email authentication method that protects domains against spoofing attacks. A spoofing attack manipulates the emails’ From field and a spoofed email message comes from a forged domain or organization. DKIM prevents these attacks from happening by adding a digital signature to the emails. Every time an email is sent, DKIM checks the time of email modification and the time of receiving it to see if any changes happened to the From address or email content. Without using DKIM, emails sent from a domain are more likely to be marked and located in a Spam box.
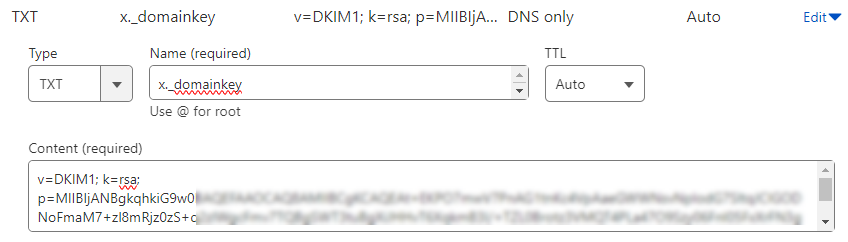
How to implement a DKIM record for email authentication?
To add a DKIM key to your DNS records, you need to first find the DKIM key on your server hosting your domain or contact your host provider. It is important to consider that the DKIM key is unique for each domain and if you own different domains, you need specific keys for each domain. After accessing the DKIM key, you need to define a DNS TXT record to add the key.
3. DMARC record
DMARC is another email authentication method that prevents email attacks like phishing and spoofing and helps the messages not be flagged as spam. This standard uses SPF and DKIM to authorize emails and informs the email receiver server about what to do next with the emails from a domain’s side that do not pass the authentication methods SPF and DKIM. By using DMARC, you will be able to access a report of the emails, which are sent from your domain or organization side, from the email receiving server. Therefore, you will have useful information about the details of the emails which can help you find suspicious activities and authentication problems.
How to configure a DMARC record to monitor and implement policies?
To implement a DMARC record, you need to first add SPF and DKIM DNS records as explained earlier in the content. Then:
- In your DNS records list, add a DNS TXT record.
- Add a name in the TXT record name field. The name for the DMARC record should be written like: _dmarc.example.com (you should replace example.com with your domain)
- Add the DMARC value to the TXT content field following this model: v=DMARC1; p=none; rua=mailto:[email protected]
- Save the changes.
Here is an example of detailed DMARC record:
v=DMARC1; p=reject; rua=mailto:[email protected], mailto:[email protected]; pct=100; adkim=s; aspf=sDMARC tags details:
| DMARC tag | Requirement | Tag values and descriptions |
| v | Required | Shows the version of DMARC and it should be set to DMARC1. |
| p | Required | Shows the instruction for the mail receiving server to what to do with unauthorized messages. |
| pct | Optional | Shows the percentage of emails to be checked. Default is 100%. Useful for testing. |
| rua | Optional | Set email addresses for receiving DMARC reports. Use mailto: prefix. |
| ruf | Optional | Send reports of unsuccessful emails. |
| sp | Optional | Set DMARC policies for subdomains. |
| adkim | Optional | Defines strictness for DKIM signature alignment. |
| aspf | Optional | Defines strictness for SPF alignment. |
| DMARC Tag | Subcategory | Description |
| p | p=none | No action taken on unauthorized messages. |
| p=quarantine | Marks unauthorized messages as spam. | |
| p=reject | Rejects unauthorized messages. |
| DMARC Tag | Subcategory | Description |
| sp | sp=none | No action taken on unauthorized messages. |
| sp=quarantine | Marks unauthorized messages as spam. | |
| sp=reject | Rejects unauthorized messages and sends a bounce email. |
| DMARC Tag | Subcategory | Description |
| adkim | adkim=s | Strict alignment, sender domain must exactly match the domain in the DKIM header. |
| adkim=r | Relaxed alignment, subdomains are accepted. |
| DMARC Tag | Subcategory | Description |
| aspf | aspf=s | Strict alignment, sender From: header must exactly match the domain in the SPF. |
| aspf=r | Relaxed alignment, subdomains are accepted. |
Alignment shows how close the email From: header matches with the domain defined in the DKIM and SPF records.
Before adding the DMARC record, make sure there has been not any other DMARC record. If any exists, you can update it based on the new changes in the DMARC policy you want to make.
Troubleshooting email DNS records issues
If one of any of the situations below happens to the emails that are sent from your domain, you need to follow the DMARC issues troubleshooting steps:
- If emails are failing DMARC.
- If emails are rejected by the receiving server.
- If emails are sent to the receivers’ Spam box.
To start troubleshooting:
1. Ensure all the DMARC configurations have been done correctly and completely.
2. Ensure that the SPF and DKIM records have been defined and are enabled. Consider that they should be enabled at least two days before enabling the DMARC record.
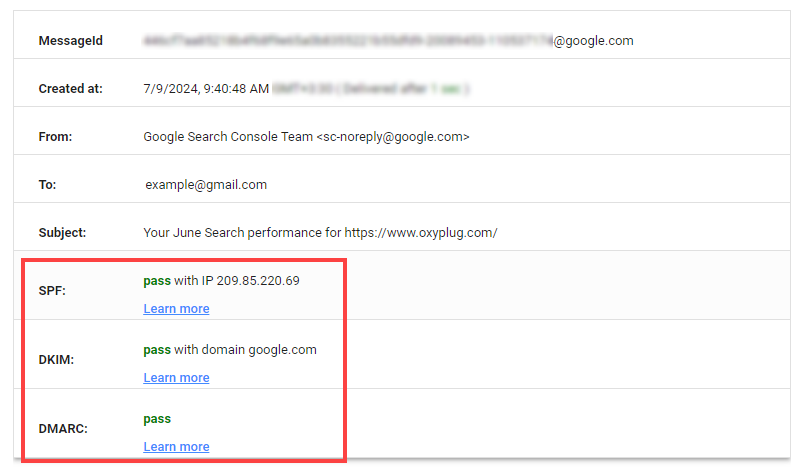
3.Check the email message header to see SPF, DKIM, and DMARC authentication check results. If you are a Gmail user, you can open an email that you are going to check, and on the right side of the page, click on the 3-dots icon which is located next to the reply
icon, then find Show original option and click on it. In the opened window, you can see the results of SPF, DKIM, and DMARC checks.
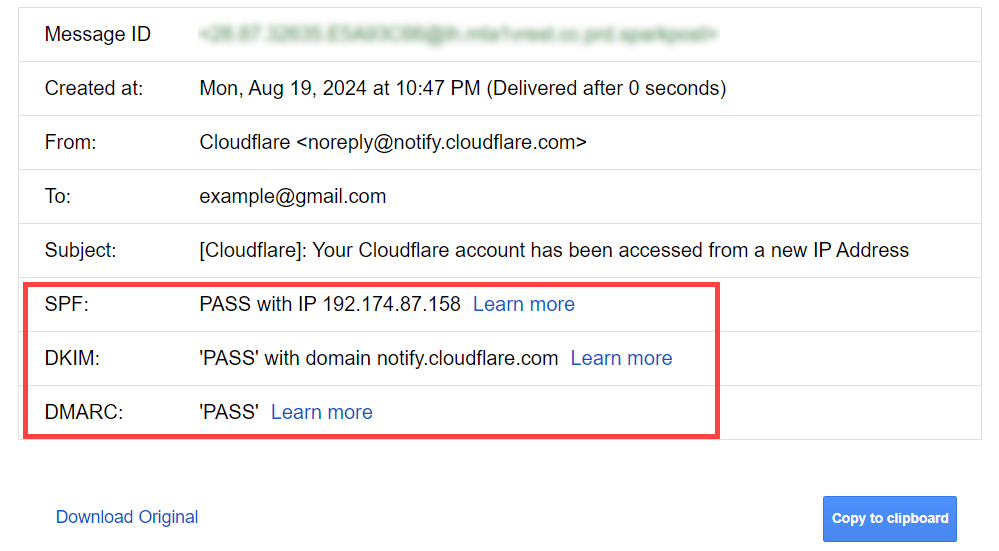
As shown above, you can simply access your email header by choosing the “Show original” option in Gmail, but if you are another email service provider’s user, you can find your email headers based on their guide and check them in Google Admin Toolbox Message header. You will see the SPF, DKIM, and DMARC authentication checks in the result.
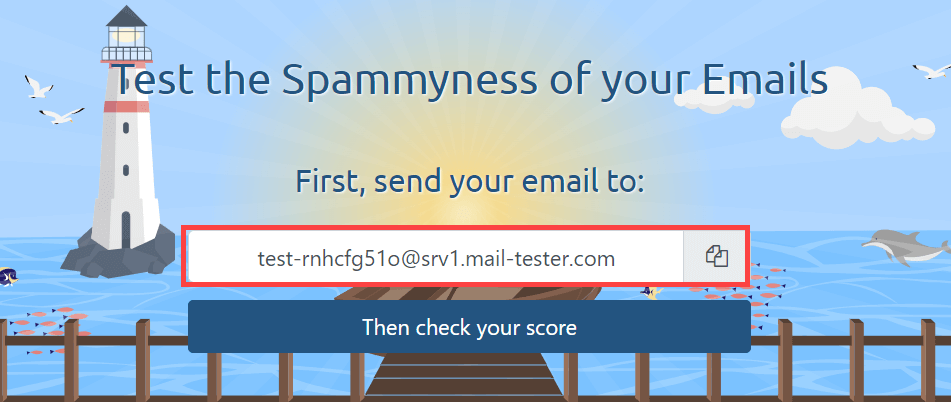
Another way to see if an email passes SPF, DKIM, and DMARC is to test your email using a mail tester. To start working with it, you need to send an email from the address that you are going to investigate to the random email address that is shown on the mail tester website.
4. If outgoing emails are valid but they fail DMARC, the problem is in DMARC policy. To troubleshoot and resolve this issue:
- Check if SPF and DKIM settings have been done correctly and emails pass their authentication policies.
- Check DMARC policy alignment. Sometimes strict DMARC alignment can cause the emails to be sent into a Spam box or rejected.
- Check the DMARC reports that you receive daily to find the emails that have problems passing SPF, DKIM, or DMARC authentication policies.
Requirements for bulk email senders
As the importance of email security is increasing significantly, popular email platforms like Google and Yahoo have stricter rules for email senders, specifically bulk senders. All the email senders should define SPF and DKIM records for the domains that they send emails from. The bulk senders must also have a DMARC policy for preventing email attacks like spoofing or phishing.
Another important requirement for bulk email senders is to have an unsubscribe option. If you send subscription emails (especially more than 5000 per day), a one-click unsubscribe link in the email body text must exist. You need to add both of the headers below to your outgoing emails:
List-Unsubscribe-Post: List-Unsubscribe=One-Click
List-Unsubscribe: <https://example.com/unsubscribe/example>Conclusion
In conclusion, maintaining email security is crucial for email senders to protect their communication against email attacks like phishing or being flagged as spam. To safeguard emails, it is important to have important email security DNS records like SPF and DKIM defined. If you are a bulk email sender, then it is strongly recommended to add a DMARC record as well which works based on SPF and DKIM checks. These records validate the email-sending server or domain and prevent emails from being moved to spam boxes.
📚Resources:
FAQs about email security records
A SPF record is a DNS TXT record that is used for authenticating sent emails by checking if the sending server IP or domain is listed in SPF record or not.
A DKIM record is a DNS TXT record that is used for email authentication. DKIM adds a digital signature to the emails’ headers to prevent spoofing attacks. By defining a DKIM DNS record, the receiving server checks the validity of the digital signature located in the emails header using the public key in the DKIM DNS record.
A DMARC policy is a way of email authentication which helps the domain owners protect their domains from illegal uses such as spoofing and phishing. DMARC works based on the SPF and DKIM authentication results and decides what to do next if any of the mentioned protocols is not passed.
SPF and DKIM records are not obligatory, but from an email security perspective, these two are Highly Recommended.
Google Admin Toolbox Messageheader, mail-tester.com, and MXToolbox DMARC Check are some of the common tools for checking DMARC.
The “p” and “v” tags are required in a DMARC record. The “p” tag shows the further actions with unauthorized messages to be done by the email receiving server and the “v” tag shows the DMARC version which should be DMARC1.
If you send emails less than 5000 per day, you need to set SPF and DKIM as mandatory records (also better to have a DMARC record too), but if you are a bulk email sender (>5000 emails/day), a DMARC record is required as well.
No, it is not possible to have multiple DMARC records for a domain as each domain should have only a unique DMARC record.
No, it is not possible to have multiple SPF records for a domain, but you have a single SPF record which contains multiple domains and IPs.
Great article! Always keeps it engaging. Learned a lot about Email Protection. Eager to see what they share next.